DNS Queries
731.165k
Blocked Queries
5.808k
Connections
746
Updated
13 seconds ago
Frequently Asked Questions
What is PrivacyDNS?
PrivacyDNS is a DNS that protects your devices from unwanted content, such as advertisements and tracking, without installing any client-side software. Instead of installing adblockers on every device and every browser, you can use PrivacyDNS DNS once on your network and it will protect all of your devices. Because it works differently than a browser-based ad-blocker, PrivacyDNS also block ads in non-traditional places, such as in games and on smart TVs.
A legitimate website is being blocked, what can I do?
In case a legitimate website is being blocked, please report it as false positive
Do you keep logs? If so, what information do you hold and for how long?
No information being stored! We DO KEEP logs only of request count, but we DO NOT know who the request made.
Which upstream DNS servers does PrivacyDNS use?
All instances use their own, local, recursive DNS server, powered by unbound. The reason for that is simple:
After applying the blocking lists, requests made by the clients are forwarded to configured upstream DNS server(s). However, as has been mentioned by several users in the past, this leads to some privacy concerns as it ultimately raises the question: Whom can you trust? Recently, more and more small (and not so small) DNS upstream providers have appeared on the market, advertising free and private DNS service, but how can you know that they keep their promises? Right, you can't.
Furthermore, from the point of an attacker, the DNS servers of larger providers are very worthwhile targets, as they only need to poison one DNS server, but millions of users might be affected. Instead of your bank's actual IP address, you could be sent to a phishing site hosted on some island. This scenario has already happened and it isn't unlikely to happen again...
When you operate your own (tiny) recursive DNS server, then the likeliness of getting affected by such an attack is greatly reduced.
DNSCrypt & Anonymized DNSCrypt
The DNSCrypt protocol authenticates and encrypts DNS requests between DNS clients and DNS resolvers. It prevents third parties (e. g. your ISP) to spy on or tamper with your DNS requests. It uses cryptographic signatures to verify that responses originate from the chosen DNS resolver.
Anonymized DNS
DNS encryption was a huge step towards making DNS more secure, preventing intermediaries from recording and tampering with DNS traffic.
However, one still has to trust non-logging DNS servers for actually doing what they pretend to do. They obviously see the decrypted traffic, but also client IP addresses.
In order to prevent this, using DNS over Tor or over proxies (HTTP, SOCKS) has become quite common. However, this is slow and unreliable as these mechanisms were not designed to relay DNS traffic.
Anonymized DNS prevents servers from learning anything about client IP addresses, by using intermediate relays dedicated to forwarding encrypted DNS data.
How does it work?
Instead of directly reaching a server, that is one of the public resolvers, an Anonymized DNS client encrypts the query for the final server, but sends it to a relay.
The relay doesn't know the secret key, and cannot learn anything about the content of the query. It can only blindly forward the query to the DNS recursive resolver, the only server that can decrypt it.
The DNS resolver itself receives a connection from the relay, not from the actual client. So the only IP address it knows about is the IP of the relay, making it impossible to map queries to clients
Anonymized DNSCrypt
Anonymized DNS can be implemented on top of all existing encrypted protocols, but DNSCrypt is by far the simplest and most efficient instantiation.
It only adds a header with a constant sequence followed by routing information (server IP+port) to unmodified DNSCrypt queries. Implementing it on top of an existing DNSCrypt implementation is trivial.
The overhead is minimal. Unlike DoH where headers may still reveal a lot of information about the client's identity, Anonymized DNSCrypt, by design, doesn't allow passing any information at all besides the strict minimum required for routing.
For relay operators, Anonymized DNSCrypt is less of a commitment than running a Tor node. Queries can only be relayed over UDP, they need to match a very strict format, amplification is impossible, and loops are prevented. Relays can essentially be only used for encrypted DNS traffic.
To test DNSCrypt you can use following code:
dig @dnscrypt.hungary.privacy-dns.pw A whoami.akamai.net +short -p 11111 dig @anonymized.dnscrypt.hungary.privacy-dns.pw A whoami.akamai.net +short -p 16661
Is PrivacyDNS free from DNS Cache Poisoning?
Yes, PrivacyDNS passes the DNS Nameserver Spoofability Test by GRC, which checks for Cache Poisoning.
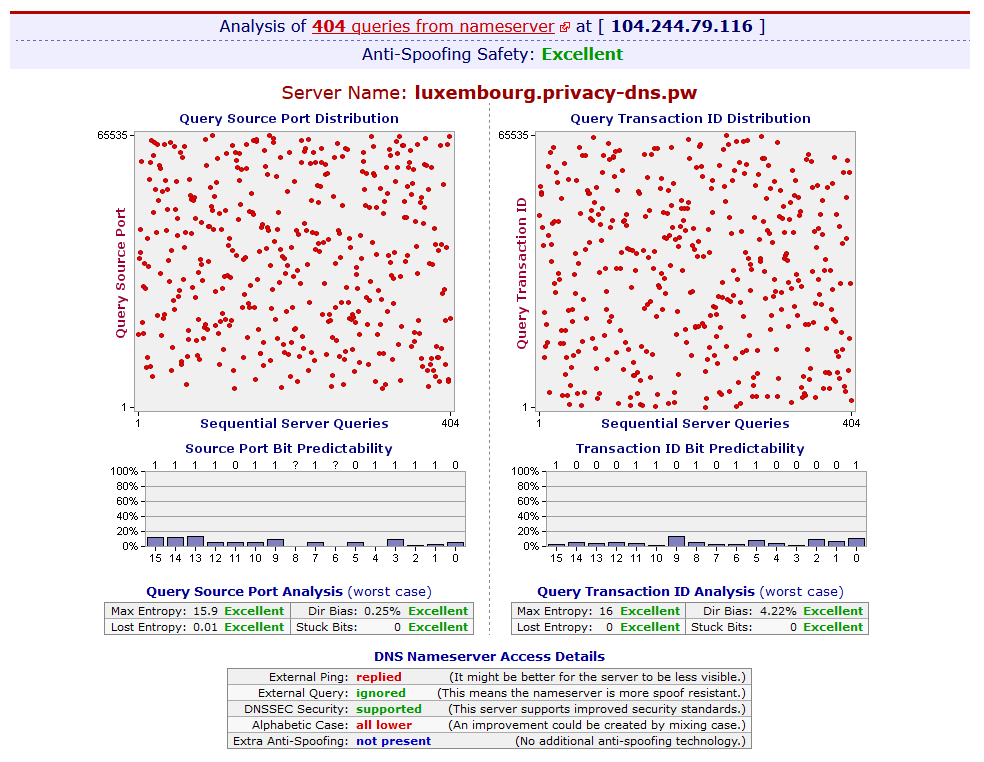
How can I check if I’m using PrivacyDNS?
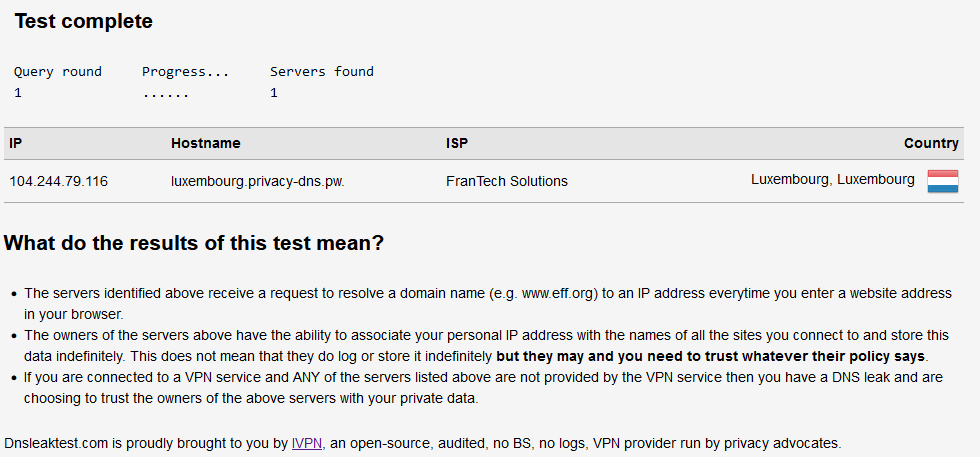
After configuring your device to use PrivacyDNS, navigate to dnsleaktest.com and run a standard (or extended) test. ONLY *.privacy-dns.pw should show up as hostname(s) the results table, like shown below.
How can I check PrivacyDNS DoH?
curl -D - "https://luxembourg.privacy-dns.pw/dns-query?ct&dns=q80BAAABAAAAAAAAB2V4YW1wbGUDY29tAAABAAE" | hexdump -c
00000000 H T T P / 1 . 1 2 0 0 O K \r 0000010 \n S e r v e r : n g i n x \r \n 0000020 D a t e : M o n , 0 3 J a 0000030 n 2 0 2 2 1 4 : 2 0 : 5 0 0000040 G M T \r \n C o n t e n t - T y p 0000050 e : a p p l i c a t i o n / d 0000060 n s - m e s s a g e \r \n C o n t 0000070 e n t - L e n g t h : 4 5 \r \n 0000080 C o n n e c t i o n : k e e p 0000090 - a l i v e \r \n A c c e s s - C 00000a0 o n t r o l - A l l o w - O r i 00000b0 g i n : h t t p : / / 1 2 7 . 00000c0 0 . 0 . 1 : 4 4 4 \r \n V a r y : 00000d0 O r i g i n \r \n \r \n ▒ ▒ 201 200 \0 00000e0 001 \0 001 \0 \0 \0 \0 \a e x a m p l e 003 00000f0 c o m \0 \0 001 \0 001 ▒ \f \0 001 \0 001 \0 001 0000100 P ▒ \0 004 ] ▒ ▒ " 0000108
How can I verify PrivacyDNS TLS connection?
echo | openssl s_client -connect 'luxembourg.privacy-dns.pw:853'
CONNECTED(00000005)
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = E6
verify return:1
depth=0 CN = luxembourg.privacy-dns.pw
verify return:1
---
Certificate chain
0 s:CN = luxembourg.privacy-dns.pw
i:C = US, O = Let's Encrypt, CN = E6
1 s:C = US, O = Let's Encrypt, CN = E6
i:C = US, O = Internet Security Research Group, CN = ISRG Root X1
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIDkTCCAxigAwIBAgISBFzzPZSELwkyqPTzbaorwEP6MAoGCCqGSM49BAMDMDIx
CzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQDEwJF
NjAeFw0yNDA5MTgxNTU0NDZaFw0yNDEyMTcxNTU0NDVaMCQxIjAgBgNVBAMTGWx1
eGVtYm91cmcucHJpdmFjeS1kbnMucHcwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNC
AASHkufo1GhcancUbYoYXLPy1bfvVXNf7HJNN4EXUGEX3NZlvWMMWuHZ0dcPkoME
Aq3u6VfKXg4qYN/KM8ow6J7ro4ICGjCCAhYwDgYDVR0PAQH/BAQDAgeAMB0GA1Ud
JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMB0GA1UdDgQW
BBT0iWSiXGlVYEjovZbi7WgrVJcQbDAfBgNVHSMEGDAWgBSTJ0aYA6lRaI6Y1sRC
SNsjv1iU0jBVBggrBgEFBQcBAQRJMEcwIQYIKwYBBQUHMAGGFWh0dHA6Ly9lNi5v
LmxlbmNyLm9yZzAiBggrBgEFBQcwAoYWaHR0cDovL2U2LmkubGVuY3Iub3JnLzAk
BgNVHREEHTAbghlsdXhlbWJvdXJnLnByaXZhY3ktZG5zLnB3MBMGA1UdIAQMMAow
CAYGZ4EMAQIBMIIBAwYKKwYBBAHWeQIEAgSB9ASB8QDvAHYASLDja9qmRzQP5WoC
+p0w6xxSActW3SyB2bu/qznYhHMAAAGSBg1w/AAABAMARzBFAiEA/DhK1VVOQTSa
VEnmyllg3y4kgv7F/UnbD49rN5z8FQACIDswmEOQg88N62h22Od9i/bdDJ60JIs0
ARr8wKBDzeCXAHUA3+FW66oFr7WcD4ZxjajAMk6uVtlup/WlagHRwTu+UlwAAAGS
Bg1xyQAABAMARjBEAiBsNRu2/0waiK8RC1+cpAy2OoxT3mZH7fx0/en/hXFJxwIg
R+tZGao221gU/d05WIZt98cmtdxrgXTUBCeUXP/iUlIwCgYIKoZIzj0EAwMDZwAw
ZAIwGjCFIdFbfsm0COXjyQM5C+beeEnoVRpnDTRh79SCNjrDpcltp6LvXnpuru2e
vFfWAjBrNtqkDE7iIEsdrLprTzJBg80dT3rcG4sDsak+nkxBWIHxD7vzfK5TO5t8
49ktZ6U=
-----END CERTIFICATE-----
subject=CN = luxembourg.privacy-dns.pw
issuer=C = US, O = Let's Encrypt, CN = E6
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: ECDSA
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2391 bytes and written 391 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_128_GCM_SHA256
Server public key is 256 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_128_GCM_SHA256
Session-ID: 971E1278AC0601F391256E429DA2B1ED0DCB19B77E074328B3DBC665CEE018FA
Session-ID-ctx:
Resumption PSK: 9F1DAB4ACFE2C08652206029108A0A43A238AD349803C3B86ECB5F29C2CFB963
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 604800 (seconds)
TLS session ticket:
0000 - 87 87 04 15 e6 df 92 1a-ed 98 3f 58 02 61 dd 64 ..........?X.a.d
0010 - 37 db 1e f3 97 2d fe 20-07 6b 7a ee 4c 6f 0c 19 7....-. .kz.Lo..
0020 - d0 ad 1d 82 f5 e7 d3 ce-ab 8a 65 2f 66 58 62 2f ..........e/fXb/
0030 - 9b 90 ed 6d 4c b2 2e 9d-1f 3d aa bc 21 49 05 20 ...mL....=..!I.
0040 - 3e 78 68 d6 86 ec e0 7c-53 40 97 a1 24 51 a0 f0 >xh....|S@..$Q..
0050 - 6c 63 38 13 6c b3 00 b1-5c 9f 40 9c 68 10 e0 9e lc8.l...\[email protected]...
0060 - 4e be 73 71 af a0 d8 19-11 N.sq.....
Start Time: 1726768765
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
DONE
For kdig you will need apt install knot-dnsutils on linux.
kdig -d @luxembourg.privacy-dns.pw +tls-ca +tls-host=luxembourg.privacy-dns.pw google.com
;; DEBUG: Querying for owner(google.com.), class(1), type(1), server(luxembourg.privacy-dns.pw), port(853), protocol(TCP) ;; DEBUG: TLS, imported 137 system certificates ;; DEBUG: TLS, received certificate hierarchy: ;; DEBUG: #1, CN=luxembourg.privacy-dns.pw ;; DEBUG: SHA-256 PIN: sJek2x6dt8jnpYdbl+KUUqvkD6k2gEFCQ+qYVjGenAA= ;; DEBUG: #2, C=US,O=Let's Encrypt,CN=E6 ;; DEBUG: SHA-256 PIN: 0Bbh/jEZSKymTy3kTOhsmlHKBB32EDu1KojrP3YfV9c= ;; DEBUG: TLS, skipping certificate PIN check ;; DEBUG: TLS, The certificate is trusted. ;; TLS session (TLS1.2)-(ECDHE-ECDSA-SECP256R1)-(AES-128-GCM) ;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 40357 ;; Flags: qr rd ra; QUERY: 1; ANSWER: 1; AUTHORITY: 0; ADDITIONAL: 1 ;; EDNS PSEUDOSECTION: ;; Version: 0; flags: ; UDP size: 4096 B; ext-rcode: NOERROR ;; QUESTION SECTION: ;; google.com. IN A ;; ANSWER SECTION: google.com. 300 IN A 172.217.168.206 ;; Received 55 B ;; Time 2024-09-19 20:00:36 CEST ;; From 104.244.79.116@853(TCP) in 50.7 ms
Which DS algorithms and DNSSEC signing algorithms are supported by the PrivacyDNS?
You can check it yourself after setting up PrivacyDNS on your system. (for a test click here)
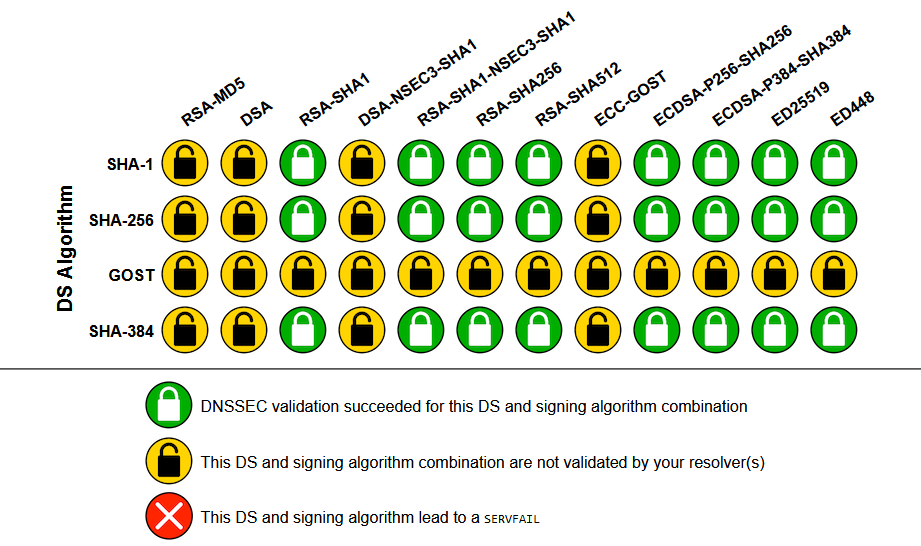
Another test (for a test click here)
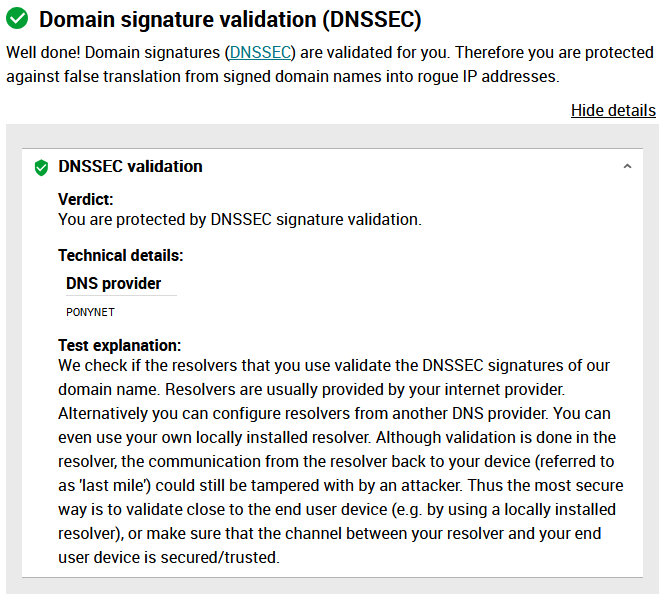
Another test (for a test click here)
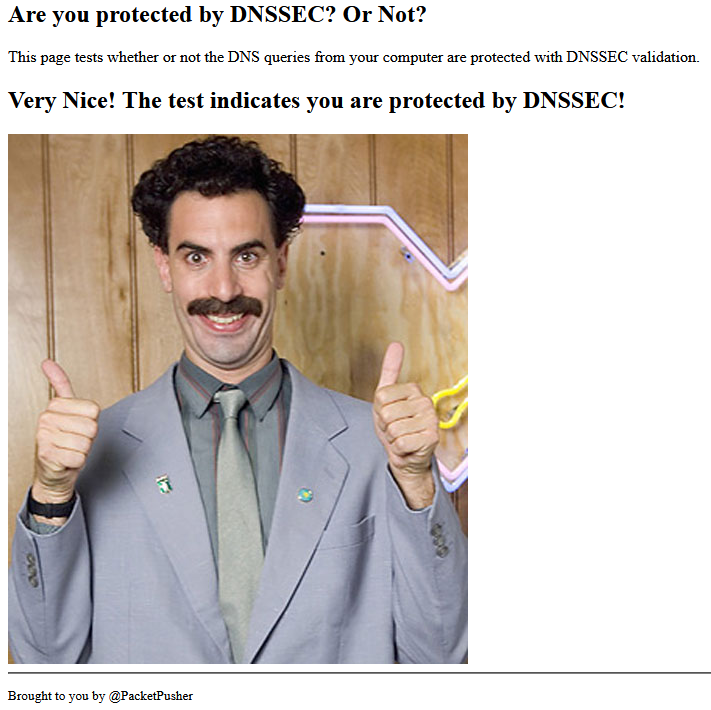
Another test (for a test click here)
And last test, you can test DNSSEC validation using
The first command should give a status report of SERVFAIL and no IP address. The second should give NOERROR plus an IP address.
dig sigfail.verteiltesysteme.net @luxembourg.privacy-dns.pw -p 53
dig sigok.verteiltesysteme.net @luxembourg.privacy-dns.pw -p 53
Where are the servers located?
See the details on the DNS Servers page. All instances are placed on fast uplinks in professional data centers.
Who is behind this service?
A group of cypherpunks.
Is DNS ANY record query available?
No! We have it disabled :)
dig ANY sigok.verteiltesysteme.net @luxembourg.privacy-dns.pw -p 53 status: NOTIMP
Do you have an uptime guarantee and/or service level agreement (SLA)?
No. This service is provided based on best effort.
Additionally, it's provided without any warranty and I renounce liability for any claim, damages or other liability arising from the use of this service.
Does PrivacyDNS block advertisements on YouTube?
YouTube serves (most of) theirs ads from the same domain they serve their video content from. Hence it's (almost) impossible for a DNS based adblocker to block YouTube ads because you cannot just block the subdomain, as it will also break video playback.
There are some hacky solutions out there, but none are stable and guaranteed to work. Most of them just break YouTube playback and it's really a cat and mouse game.
I suggest using uBlock Origin as browser plugin to block YouTube ads instead. If you own Android Smart TV, I recommend taking a look at 'Smart YouTube'. It's basically an (open source) YouTube client with built-in (client side) adblocking.